I have worked with a few customers that are annoyed with the user configuration required to use the new Silverlight SCOM web console. The web console is often used for one-off application owners or IT staff that are not regularly using SCOM. It was is a great way to give these users quick access to view the SCOM console so they can get more information about an alert they have received.
SCOM 2012 has extra steps that an end user has to take to get the web console to work. Users see the “Web Console Configuration Required” screen and are often confused as to what do to.
To fix this we can automate the configuration process. This will remove the configuration screens and the end user can access the SCOM web console easily.
Here are my sample GPOs with instructions on how to install them.
Download: https://www.scom2k7.com/downloads/SCOM_Web_Console.zip
The instructions below will walk you through creating your own GPOs to automate the process.
Here are the high level steps.
- Automate Install of Microsoft Silverlight
- Export Client Certificate
- Export Registry Key(s)
- Automate Install of Client Certificate
- Automate Install of Registry Key(s)
- Verify it works on Windows XP, Vista, 7, and 8
1. Automate Install of Microsoft Silverlight
The first page users are presented with is to install Microsoft Silverlight
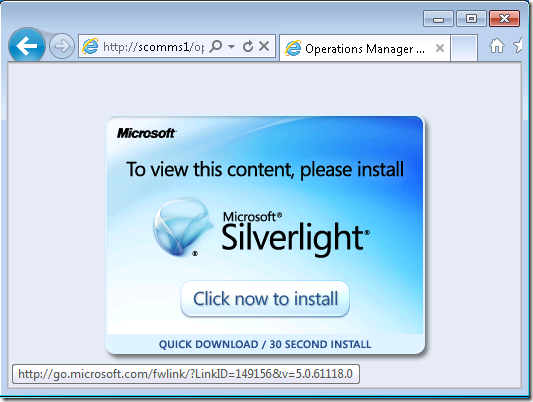
There are multiple ways to automate this install. I recommend creating a SCCM package or login script to push the install out to the clients that need it.
To do an unattended installed, the command(s) you need.
Silverlight_x64.exe /q or Silverlight.exe /q
Download Silverlight - http://go.microsoft.com/fwlink/?LinkID=149156&v=5.0.61118.0
My next challenge is the Web Console Configuration Required screen. This is the screen that throws off end users as they think the web console is not working and something need to be configured on the backend.
2. Export Client Certificate
First I click configure and download the SilverlightClientConfiguration.exe.
The tool does two things. Creates a certificate and creates a registry key.
Now I need to export the client certificate.
I select Computer account, Local computer, Finish, OK 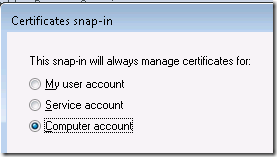
Then I expand down to Trusted Publishers, Certificates 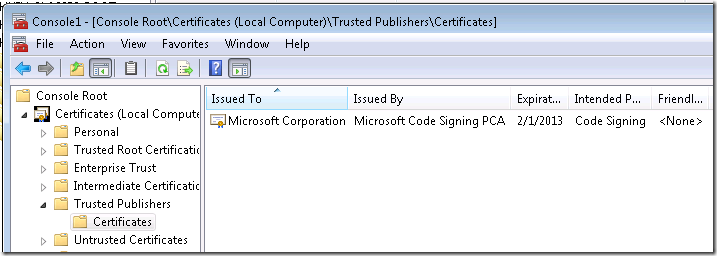
I right click on the Microsoft Code Signing PCA certificate and export it.
I save it as a DER encoded binary 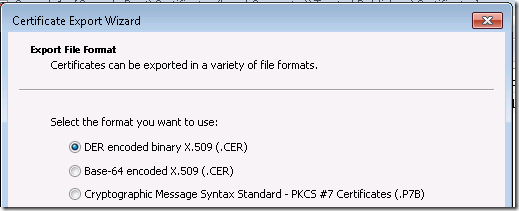
I pick a location to save the file and Finish. 
3. Export Registry Key(s)
I open the registry editor
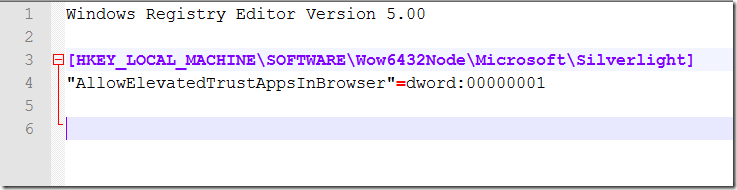
I go to “HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Silverlight” and export the Key 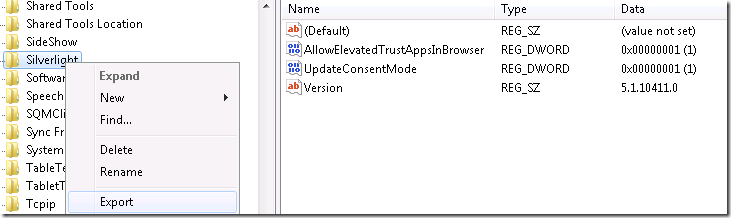
I open the file in notepad and remove everything but
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Silverlight]
"AllowElevatedTrustAppsInBrowser"=dword:00000001
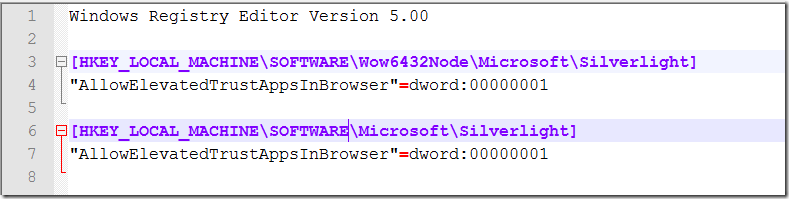
I also create the same key but for 32-bit systems by removing the Wow6432Node
You can download my copy here. Link
If you know how to add the cert and registry key into AD you can stop reading here. I will go though the process for anyone who doesn’t know how.
4. Automate Install of Client Certificate
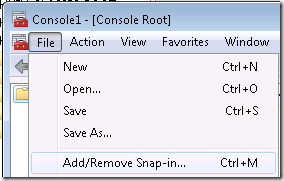
To automate the install of the client certificate and registry keys I will use Active Directory Group Policy Objects.
I log into my domain controller and launch the Group Policy Management Console 
I right click on my domain and create a OU called SCOM Web Console. (If you already have a OU that contains the computers want to deploy to you can skip this step) 
I right click on the OU I created and choose Create a GPO in this domain, and link it here.. 
I call the GPO SCOM Web Console Components x64. I will need two GPOs. One for 32-bit machines and one for 64-bit machines. 
I then right click on the GPO and edit it. 
In the navigation pane, I open Computer Configuration\Policies\Windows Settings\Security Settings\Public Key Policies\Trusted Publishers
I click next and browse to the certificate I exported earlier 
I leave the default Trusted Publishers 
I click next, and Finish
I use repeat the process to create a GPO for 32-bit systems 
Now I have two GPOs with the same certs and configuration 
5. Automate Install of Registry Key(s)
I go back to the same policies I created earlier and edit them.
I start with the 64-Bit policy and go to Computer Configuration\Preferences\Windows Settings\Registry  64-
64-
I create a New, Registry Item. 
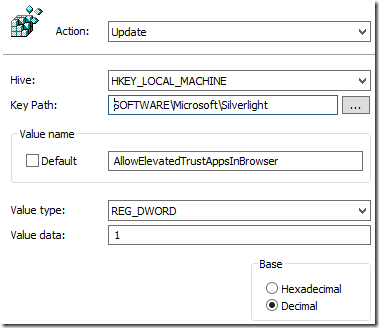
In the Key Path for the 64-bit GPO I add
SOFTWARE\Wow6432Node\Microsoft\Silverlight
For the Value name I type
AllowElevatedTrustAppsInBrowser
I change the Value type to Reg_DWORD
Then I change the Base to Decimal and for Value data I type in 1 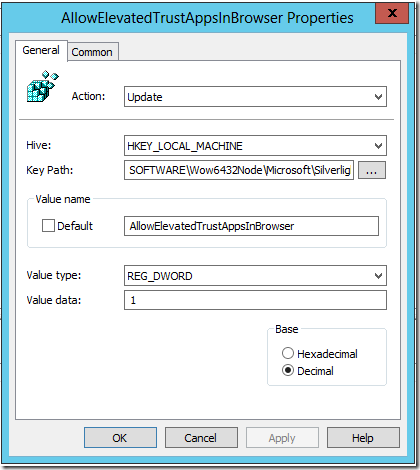
I click ok.
I repeat the process for the 32-bit one but I add this registry key.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Silverlight
Now I need to create some WMI filters to filter if it’s a 32-bit or 64-bit system. (Wow this more work then I thought!)
I go back into my Group Policy Management console.
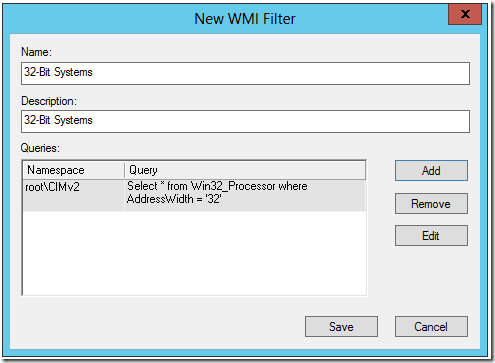
Under WMI Filters I right click and select New.. 
I call the first one 64-Bit Systems. For the Description I use the same.
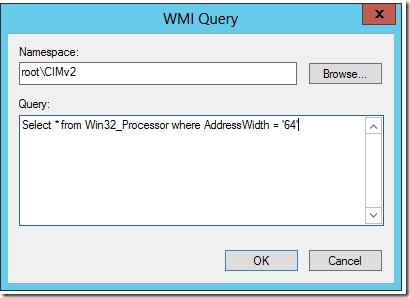
I click add. Then I Add this query.
Select * from Win32_Processor where AddressWidth = ’64’
I click OK and it looks like this. 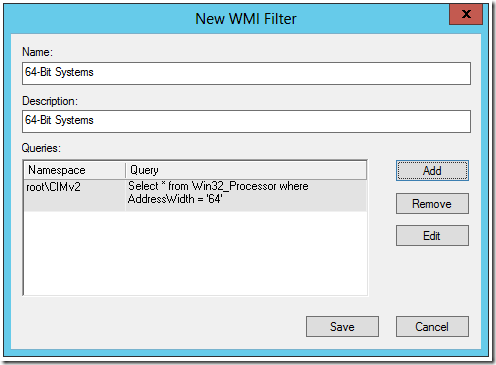
I click Save and I repeat the process for the 32-Bit Filter.
But I use this query
Select * from Win32_Processor where AddressWidth = ’32’
I next attach the filters to the GPOs I created earlier.
I go back to the SCOM Web Console Components x64 GPO and click on it 
At the bottom of the screen I go to WMI Filtering 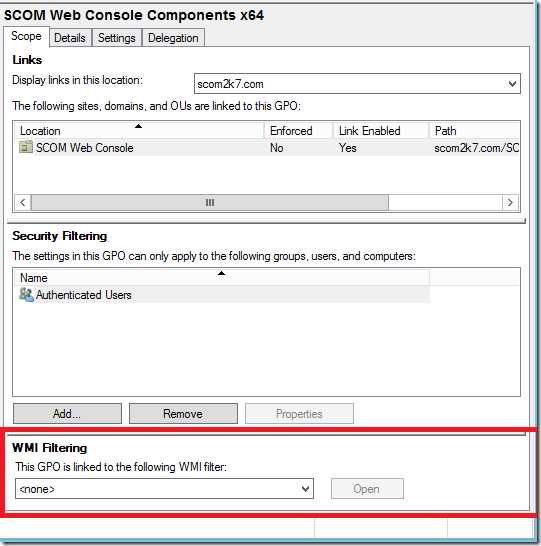
I select 64-Bit Systems and click Yes 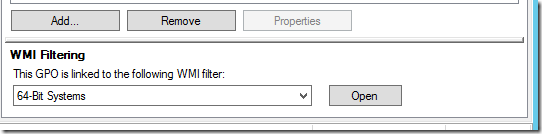
I repeat the process to attach the 32-Bit filter to the 32-Bit GPO
I now have the filters set and I am done. 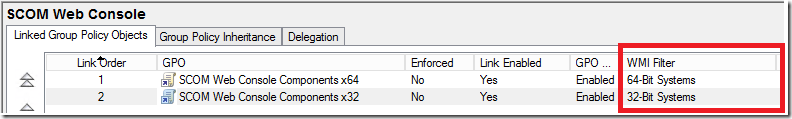
Now I just add my clients to OU and they will get the new policy. 
5. Verify it works on Windows XP, Vista, 7, and 8
I log into one of my clients, open a command prompt and type gpupdate /force to force the group policy down. 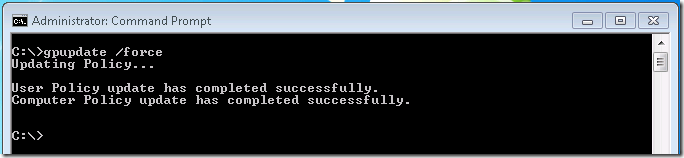
I type in the address of the SCOM 2012 web console and it works without any prompts! 
I have tested this on Win8, Win7 SP1 (64-Bit), Win7 SP1(32-Bit), Vista SP2(32-Bit), and XP SP3 (32-bit)
*Note with Windows XP SP3 I had to install the Group Policy Preference Client Side Extensions for Windows XP – http://www.microsoft.com/en-us/download/details.aspx?displaylang=en&id=3628. In SP3 these are supposed to be already installed but I couldn’t get the registry group policies to work without reinstalling the GPO extensions.
This is good information, i have been struggling with this issue for a month now
This is really good; thanks for sharing the info!
A bit more information from TechNet on the registry values: Enable Trusted Applications to Run Inside the Browser http://msdn.microsoft.com/en-us/library/gg192793(VS.95).aspx
Specifically: Ensure that you do not set conflicting registry keys. For more information, see the AllowInstallOfElevatedTrustApps and AllowLaunchOfElevatedTrustApps registry keys in Group Policy Settings. Specifically, you can disallow the installation of trusted applications without affecting their in-browser use. However, disallowing the launch of trusted applications will cause them to run in partial trust, even inside the browser.
Thank you! You turned what I thought was going to be another packaging job (which I hate) into a simple GPO deployment (which I “not hate” ) 🙂 You’re a Boss…
Used this today and it worked out great!
just curious why you chose to have two separate GPOs with WMI filters instead of a single GPO using item-level targeting on each registry preference. item-level targeting would let you check to see if the SOFTWARE\Wow6432Node exists in the registry, or you could still do the same wmi query.
also I note that you posted this on 9/2012 and the certificate was set to expire 1/2013. do we need to manually keep importing updated versions of that certificate into the GPO?
The Silverlight Web Console Configuration tool (SilverlightClientConfiguration.exe) primarily installs a registry key (HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Silverlight), sets the AllowElevatedTrustAppsInBrowser to 1, and loads a cert under Trusted Publishers/Certificates. Since we are deploying this tool to hundreds of workstations, there does not appear to be an Add/Remove option to remove the tool. Manually is possible, but is not the preferred method, please advise.
what a bunch of horshit hoops to jump through to get this to work.